Download AWS Certified Security - Specialty.SCS-C02.VCEplus.2024-01-16.45q.vcex
| Vendor: | Amazon |
| Exam Code: | SCS-C02 |
| Exam Name: | AWS Certified Security - Specialty |
| Date: | Jan 16, 2024 |
| File Size: | 237 KB |
| Downloads: | 13 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A company wants to monitor the deletion of customer managed CMKs A security engineer must create an alarm that will notify the company before a CMK is deleted The security engineer has configured the integration of IAM CloudTrail with Amazon CloudWatch
What should the security engineer do next to meet this requirement?
- Use inbound rule 100 to allow traffic on TCP port 443 Use inbound rule 200 to deny traffic on TCP port 3306 Use outbound rule 100 to allow traffic on TCP port 443
- Use inbound rule 100 to deny traffic on TCP port 3306. Use inbound rule 200 to allow traffic on TCP port range 1024-65535. Use outbound rule 100 to allow traffic on TCP port 443
- Use inbound rule 100 to allow traffic on TCP port range 1024-65535 Use inbound rule 200 to deny traffic on TCP port 3306 Use outbound rule 100 to allow traffic on TCP port 443
- Use inbound rule 100 to deny traffic on TCP port 3306 Use inbound rule 200 to allow traffic on TCP port 443 Use outbound rule 100 to allow traffic on TCP port 443
Correct answer: A
Question 2
A company is hosting a static website on Amazon S3 The company has configured an Amazon CloudFront distribution to serve the website contents The company has associated an IAM WAF web ACL with the CloudFront distribution. The web ACL ensures that requests originate from the United States to address compliance restrictions.
THE company is worried that the S3 URL might still be accessible directly and that requests can bypass the CloudFront distribution
Which combination of steps should the company take to remove direct access to the S3 URL? (Select TWO. )
- Select 'Restrict Bucket Access' in the origin settings of the CloudFront distribution
- Create an origin access identity (OAI) for the S3 origin
- Update the S3 bucket policy to allow s3 GetObject with a condition that the IAM Referer key matches the secret value Deny all other requests
- Configure the S3 bucket poky so that only the origin access identity (OAI) has read permission for objects in the bucket
- Add an origin custom header that has the name Referer to the CloudFront distribution Give the header a secret value.
Correct answer: AD
Question 3
A company's security team is building a solution for logging and visualization. The solution will assist the company with the large variety and velocity of data that it receives from IAM across multiple accounts. The security team has enabled IAM CloudTrail and VPC Flow Logs in all of its accounts. In addition, the company has an organization in IAM Organizations and has an IAM Security Hub master account.
The security team wants to use Amazon Detective However the security team cannot enable Detective and is unsure why
What must the security team do to enable Detective?
- Enable Amazon Macie so that Secunty H jb will allow Detective to process findings from Macie.
- Disable IAM Key Management Service (IAM KMS) encryption on CtoudTrail logs in every member account of the organization
- Enable Amazon GuardDuty on all member accounts Try to enable Detective in 48 hours
- Ensure that the principal that launches Detective has the organizations ListAccounts permission
Correct answer: D
Question 4
An application team wants to use IAM Certificate Manager (ACM) to request public certificates to ensure that data is secured in transit. The domains that are being used are not currently hosted on Amazon Route 53
The application team wants to use an IAM managed distribution and caching solution to optimize requests to its systems and provide better points of presence to customers The distribution solution will use a primary domain name that is customized The distribution solution also will use several alternative domain names The certificates must renew automatically over an indefinite period of time
Which combination of steps should the application team take to deploy this architecture? (Select THREE.)
- Request a certificate (torn ACM in the us-west-2 Region Add the domain names that the certificate will secure
- Send an email message to the domain administrators to request vacation of the domains for ACM
- Request validation of the domains for ACM through DNS Insert CNAME records into each domain's DNS zone
- Create an Application Load Balancer for me caching solution Select the newly requested certificate from ACM to be used for secure connections
- Create an Amazon CloudFront distribution for the caching solution Enter the main CNAME record as the Origin Name Enter the subdomain names or alternate names in the Alternate Domain NamesDistribution Settings Select the newly requested certificate from ACM to be used for secure connections
- Request a certificate from ACM in the us-east-1 Region Add the domain names that the certificate wil secure
Correct answer: CDF
Question 5
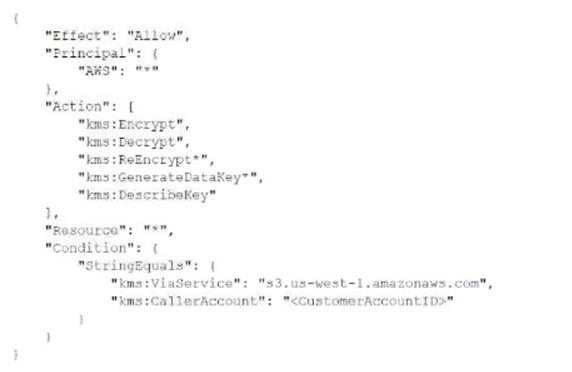
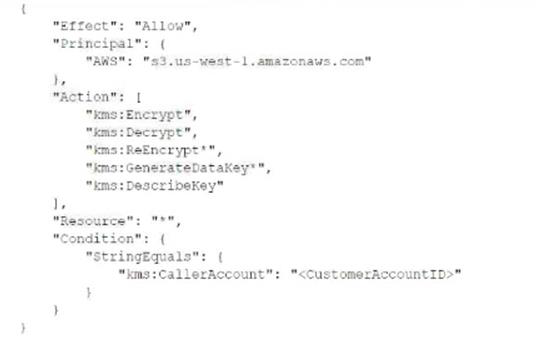
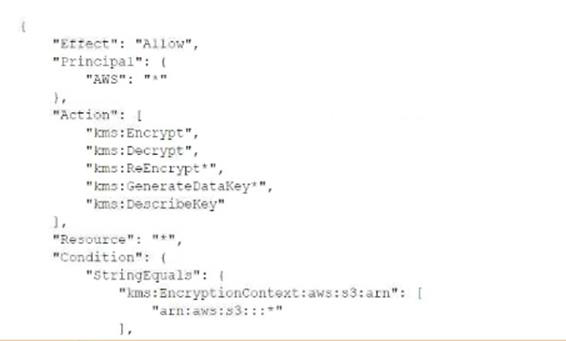
A security engineer needs to create an IAM Key Management Service <IAM KMS) key that will De used to encrypt all data stored in a company's Amazon S3 Buckets in the us-west-1 Region. The key will use serverside encryption. Usage of the key must be limited to requests coming from Amazon S3 within the company's account.
Which statement in the KMS key policy will meet these requirements?
Correct answer: A
Question 6
A business requires a forensic logging solution for hundreds of Docker-based apps running on Amazon EC2. The solution must analyze logs in real time, provide message replay, and persist logs.
Which Amazon Web Offerings (IAM) services should be employed to satisfy these requirements? (Select two.)
- Amazon Athena
- Amazon Kinesis
- Amazon SQS
- Amazon Elasticsearch
- Amazon EMR
Correct answer: BD
Question 7
Within a VPC, a corporation runs an Amazon RDS Multi-AZ DB instance. The database instance is connected to the internet through a NAT gateway via two subnets.
Additionally, the organization has application servers that are hosted on Amazon EC2 instances and use the RDS database. These EC2 instances have been deployed onto two more private subnets inside the same VPC. These EC2 instances connect to the internet through a default route via the same NAT gateway. Each VPC subnet has its own route table.
The organization implemented a new security requirement after a recent security examination. Never allow the database instance to connect to the internet. A security engineer must perform this update promptly without interfering with the network traffic of the application servers.
How will the security engineer be able to comply with these requirements?
- Remove the existing NAT gateway. Create a new NAT gateway that only the application server subnets can use.
- Configure the DB instances inbound network ACL to deny traffic from the security group ID of the NAT gateway.
- Modify the route tables of the DB instance subnets to remove the default route to the NAT gateway.
- Configure the route table of the NAT gateway to deny connections to the DB instance subnets.
Correct answer: C
Explanation:
Each subnet has a route table, so modify the routing associated with DB instance subnets to prevent internet access. Each subnet has a route table, so modify the routing associated with DB instance subnets to prevent internet access.
Question 8
A development team is attempting to encrypt and decode a secure string parameter from the IAM Systems Manager Parameter Store using an IAM Key Management Service (IAM KMS) CMK. However, each attempt results in an error message being sent to the development team.
Which CMK-related problems possibly account for the error? (Select two.)
- The CMK is used in the attempt does not exist.
- The CMK is used in the attempt needs to be rotated.
- The CMK is used in the attempt is using the CMKs key ID instead of the CMK ARN.
- The CMK is used in the attempt is not enabled.
- The CMK is used in the attempt is using an alias.
Correct answer: AD
Explanation:
https://docs.IAM.amazon.com/kms/latest/developerguide/services-parameter-store.html#parameter-store-cmk-fail https://docs.IAM.amazon.com/kms/latest/developerguide/services-parameter-store.html#parameter-store-cmk-fail
Question 9
A business stores website images in an Amazon S3 bucket. The firm serves the photos to end users through Amazon CloudFront. The firm learned lately that the photographs are being accessible from nations in which it does not have a distribution license.
Which steps should the business take to safeguard the photographs and restrict their distribution? (Select two.)
- Update the S3 bucket policy to restrict access to a CloudFront origin access identity (OAI).
- Update the website DNS record to use an Amazon Route 53 geolocation record deny list of countries where the company lacks a license.
- Add a CloudFront geo restriction deny list of countries where the company lacks a license.
- Update the S3 bucket policy with a deny list of countries where the company lacks a license.
- Enable the Restrict Viewer Access option in CloudFront to create a deny list of countries where the company lacks a license.
Correct answer: AC
Explanation:
For Enable Geo-Restriction, choose Yes. For Restriction Type, choose Whitelist to allow access to certain countries, or choose Blacklist to block access from certain countries.https://IAM.amazon.com/premiumsupport/knowledge-center/cloudfront-geo-restriction/ For Enable Geo-Restriction, choose Yes. For Restriction Type, choose Whitelist to allow access to certain countries, or choose Blacklist to block access from certain countries.
https://IAM.amazon.com/premiumsupport/knowledge-center/cloudfront-geo-restriction/
Question 10
A company has multiple departments. Each department has its own IAM account. All these accounts belong to the same organization in IAM Organizations.
A large .csv file is stored in an Amazon S3 bucket in the sales department's IAM account. The company wants to allow users from the other accounts to access the .csv file's content through the combination of IAM Glue and Amazon Athena. However, the company does not want to allow users from the other accounts to access other files in the same folder.
Which solution will meet these requirements?
- Apply a user policy in the other accounts to allow IAM Glue and Athena lo access the .csv We.
- Use S3 Select to restrict access to the .csv lie. In IAM Glue Data Catalog, use S3 Select as the source of the IAM Glue database.
- Define an IAM Glue Data Catalog resource policy in IAM Glue to grant cross-account S3 object access to the .csv file.
- Grant IAM Glue access to Amazon S3 in a resource-based policy that specifies the organization as the principal.
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!